 重要提示:
请勿将账号共享给其他人使用,违者账号将被封禁!
重要提示:
请勿将账号共享给其他人使用,违者账号将被封禁!
题目
A.Forbid relayin
B.Enforce masqueradin
C.Use an SSL certificat
D.Use strict bounds checking on arrays.
 更多“You want to secure your SMTP transmissions from sniffing attacks.How can you accomplis”相关的问题
更多“You want to secure your SMTP transmissions from sniffing attacks.How can you accomplis”相关的问题
第1题
A.
B.
C.
D.
第2题
A. MAC address
B. DNS server
C. DHCP server
D. resolve address
E. endpoint address
第3题
You want full access to the file.
People in your group should be able to read the file.
People in your group should not be able to write the file.
People outside of your group should be denied access to the file.
What are the most secure permissions you would apply to the file?()
A.Chage 700/home/myname/myfile.txt
B.Chage 744/home/myname/myfile.txt
C.Chmod 640/home/myname/myfile.txt
D.Chmod 064/home/myname/myfile.txt
第4题
You want to configure the domain controllers so that DNS only contains entries for computers that are active on the network. You also want to ensure that when users return you do not have to manually create or delete DNS entries.
How should you configure the DNS servers?
A.Configure both domain controllers with Active Directory integrated primary zones for the domain and enable secure dynamic updates for the zone.
B.Configure both domain controllers with Active Directory integrated primary zones for the domain and the secure cache against pollution option for the zone.
C.Configure both domain controllers with Active Directory integrated primary zones for the domain and enable scavenging and dynamic updates for the zone.
D.Configure both domain controllers with standard primary zones for the domain and enable scavenging for the zone.
E.Configure one server with a standard primary zone for the domain, and configure at least one server with an Active Directory integrated primary zone.
第5题
A. Disable File and Printer Sharing on the servers.
B. Disable the IIS Admin service on the servers.
C. Enable Server Message Block (SMB) signing on the servers.
D. Assign the Secure Server (Require Security) IPSec policy to the servers.
第6题
阅读理解Education as a career or a job
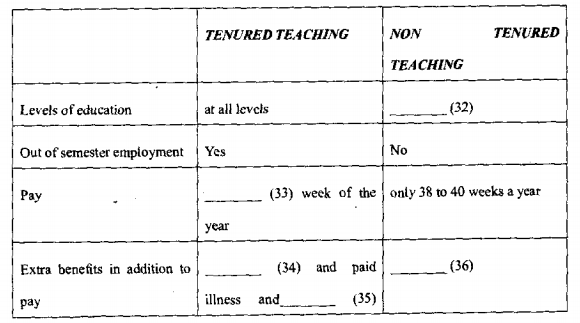
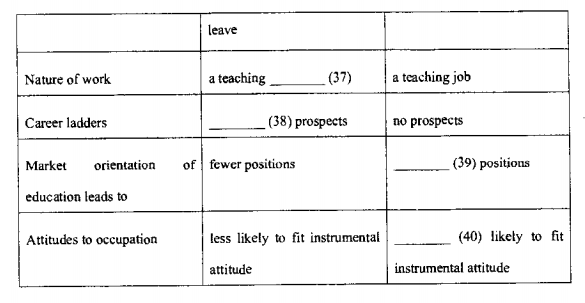
Do you want to become a teacher? If you do, then you should recognise that in England, the US and other Western countries, the term •teacher' covers a wide range of jobs which can be seen as forming an occupational hierarchy ranging from high status, high income careers to lower paid positions.
At all levels of education, university, school and kindergarten, there are a mixture of well paid, secure careers with prornotional prospects and casual jobs with no prospects. In education, if a job is a secure one, it is called tenured. If it is casual work, it is called non-tenured. Non-tenured jobs in education are paid well whilst the person is working; but out of the semester, i. e. for twelve or fourteen weeks of the year, the worker gets no employment. The tenured teacher or lecturer gets paid for every week of the year, even over the long school or university holidays. They also get extra payments that the non-tenured people do not receive. For example, they receive contributions from their employer that go towards their superannuation fund. They also get paid if they become ill or need maternity leave. When the teacher or lecturer is tenured, she or he is regarded as having a career, but the non-tenured worker is often regarded as just having a job.
The level of academic qualification and the extent of teaching experience will largely determine where a person is placed in the teaching hierarchy. However, in England now the government is asking universities to be more market-oriented and to plan research pmjects and create courses that will sell on the open market. Now that universities in England are o moving toward a more market oriented status, they are trying to find ways to save money and there is great pressure to employ more lecturers on a casual not a tenured basis.
Why do people want to become lecrurers or teachers? There is a lot of in the study of occupational choice. Many occupations have been studied to determine why people chose a particular occupation. In education, two general findings emerged: some people feel that they have a mission to teach and want to be a successful teacher, whereas others have a purely instrumental approach. An instrumental approach means that teacbing is chosen not to fulfill a lifetime ambition but just as way of earning a living. This instrumental approach is likely to develop with the casuälisation of education.
第7题
A. Junos Pulse should be configured with location awareness rules configured.
B. Odyssey Access Client should be installed with Host Checker configured to check the client‘s location.
C. Junos Pulse should be configured with all components installed.
D. Agentless access should be enabled so that clients can connect to any service without concern for installing an agent.
第8题
A.Deactivate all LM and NTLM authentication methods on the FSS1 server.
B.Use IIS to publish the confidentials files. Activate SSL on the ISS server, and then open the files as a web folder.
C.Use IPSec encryption between the FSS 1 server and the computers of the users who need to access the confidential files.
D.Use the server messager block (SMB) signing between the FSS1 server and the computers of the users who want to access the confidential files.
E.Activate offline files for the confidential files that are stored on the FSS1 server. In the folder advanced properties dialog box, select the encrypt contents to secure data option.
第9题
Henry and his friend Sally are talking about online shopping.
Sally: Do you do a lot of your shopping online?
Henry: Not really. I like looking at what's available on the Internet before I actually buy it. Sometimes, I'll choose what I want in a shop, later buying it online if it's cheaper. You don't like buying things online, do you?
Sally: No. I'm a little worried about security issues. You never know who's trying to find out your codes and passwords. Aren't you worried about that?
Henry: Not really. I know that it happens, but if you buy from reputable companies with secure websites, it should be OK. Even though I use online shopping facilities, I don't think it's the best way.
Sally: I'm surprised to hear you say that. I thought you loved any digital things.
Henry: I do. I'm a big fan of using new digital products, but I don't want to sit in front of a computer screen all day. I think people need to get out and interact with other people.
Sally: So, how about coming to the department store with me? I want to see if there are any new summer clothes on sale yet.
Henry: Sure. I'd love to join you. Can we stop by the computer store? I just want to see if they have something.
Sally: Sure. While you're in the computer store, I will visit the book store opposite. I like to browse through their books if they have anything interesting.
Henry: OK. I've finished online. Let's go. I'll just get some money and my credit card.
Sally: Thanks for reminding me. I had forgotten to get mine.
1. Both of them like online shopping very much.
2. Being cheap is one of the reasons for online shopping.
3. Henry is a big fan of digital products, so he likes sitting in front of the computer all day.
4. Henry will go to the department store with Sally.
5. Both of them will visit the computer store.
第10题
To keep certain information private and secure while providing remote access for employees; many businesses are creating intranets. An intranet is an (73) organization internet that is guarded against. outside access by a special(74)feature called a Firewall (which can be software,hardware,or a combination of the two). So, if your organization has an intranet and you want to access information on it while away from the office, all you need is Web access and the password that will allow you (75) the firewall.
(71) A.access B.make C.learn D.bring
(72) A.data B.program C.mobile D.information
(73) A.inside B.external C.inner D.internal
(74) A.safe B.safety C.security D.secure
(75) A.pass B.through C.across D.cross

 警告:系统检测到您的账号存在安全风险
警告:系统检测到您的账号存在安全风险
为了保护您的账号安全,请在“赏学吧”公众号进行验证,点击“官网服务”-“账号验证”后输入验证码“”完成验证,验证成功后方可继续查看答案!
