 重要提示:
请勿将账号共享给其他人使用,违者账号将被封禁!
重要提示:
请勿将账号共享给其他人使用,违者账号将被封禁!
题目
A. VPN establishment
B. stateful ARP lookups
C. Dynamic ARP inspection
D. Network Address Translation
E. inspection of packets at higher levels (Layer 4 and above)
 更多“Which three functions are provided by the Junos OS for security platforms?()(Choose three.)”相关的问题
更多“Which three functions are provided by the Junos OS for security platforms?()(Choose three.)”相关的问题
第1题
A. an antispam license
B. DNS servers configured on the SRX Series device
C. SMTP services on SRX
D. a UTM profile with an antispam configuration in the appropriate security policy
E. antivirus (full or express)
第2题
A.units or periods of training or education
B.independent self-contained units of a spacecraft
C.parts of an electronic system which perform a particular function
第3题
A.It might spread to another function, with the original practitioners acting as coaches.
B.It depends on having a cadre of eager participants.
C.It is similar with a process learned by Japanese martial arts students, especially those studying aikido, called shu-ha-ri.
D.It runs two-week sprints and conduct stand-up meetings three times a week.
第4题

A. It is configured and functioning correctly as an OSPF internal router.
B. It is configured and functioning correc tly as an ABR attached to stub area 4.
C. It is configured and functioning correctly as an ASBR attached to external area 4.
D. It is configured and functioning correctly as an ABR attached to totally stubby area 4.
E. It is not configured correctly to function as specified.
第5题
Flow control is a function that prevents network congestion by ensuring that(66)do not over-whelm(67)with data. There are three commonly used methods for handling network congestion.(68)is used by network devices to temporarily store bursts of excess data in memory until they can be processed.(69)are used by receiving devices to help prevent their buffers from overflowing.(70)is a flow-control scheme in which the source device requires an acknowledgment from the destination after a certain number of packets have been transmitted.
A.transmitting devices
B.transmitted devices
C.receiving devices
D.received devices
第6题
Flow control is a function that prevents network congestion by ensuring that(71)do not overwhelm(72)with data.
There are three commonly used methods for handling network congestion.(73)is used by network devices to temporarily store bursts of excess data in memory until they can be processed(74)are used by receiving devices to help prevent their buffers from overflowing.(75)is a flow-control scheme in which the source device requires an acknowledgment from the destination aider a certain number of packets have been transmitted.
A.transmitting devices
B.transmitted devices
C.receiving devices
D.received devices
第7题
A.architecture design B.modular design C.physical design D.distribution design A.data access components B.database management system C.data storage D.data entities A.data persistence B.data access objects C.database connection D.dataaccess logic A.system requirements B.system architecture C.application logic D.application program A.computers,cables and network B.clients,servers,and network C.CPUs,memories and I/O devices D.CPUs,hard disks and I/O devices
第8题
假定两个投资项目有相同的三个支付,但是每个支付相对应的概率各不相同,如下表所示:
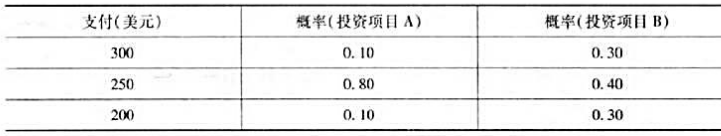
(1)求每个投资项目的期望报酬和标准差。
(2)吉尔的效用函数为U=5I,式中,I为支付。她会选择哪个投资项目?
(3)肯恩的效用函数为U=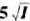 ,他会选择哪个投资项目?
,他会选择哪个投资项目?
(4)劳拉的效用函数为U=5I2,她会选择哪个投资项目?
Suppose that two investments have the same three payoffs, but the probability associated with each pay off differs,as illustrated in the table below:
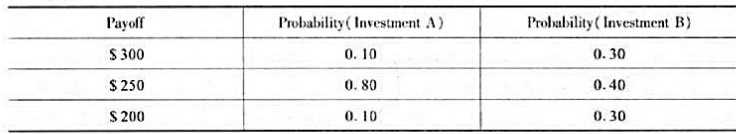
a. Find the expected return and standard deviation of each investment.
b. Jill has the utility function U=5I, where I denotes the payoff. Which investment will she choose?
c. Ken has the utility function U=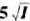 , Which investment will he choose?
, Which investment will he choose?
d. Laura has utility function U=5I2,Which investment will he choose?
第9题
A.transmitting devices
B.transmitted devices
C.receiving devices
D.received devices@@@SXB@@@A.transmitting devices
B.transmitted devices
C.receiving devices
D.received devices@@@SXB@@@A.Buffer
B.Source-quench messages
C.window
D.Windowing
E.Buffering@@@SXB@@@A.Buffer
B.Source-quench messages
C.window
D.Windowing
E.Buffering@@@SXB@@@A.Buffer
B.Source-quench messages
C.window
D.Windowing
E.Buffering
第10题
(71)
A. functional decomposition
B. object abstraction
C. data inheritance
D. information generalization
(72)
A. function model,class model and state model
B. class model,interaction model and state model
C. class model,interaction model and sequence model
D. function model,interaction model and state model
(73)
A. Static analysis
B. Semantic analysis
C. Scope analysis
D. Domain analysis
(74)
A. static structure
B. system components
C. data flows
D. program procedures
(75)
A. Program analysis
B. Function requirement
C. Application analysis
D. Physical model

 警告:系统检测到您的账号存在安全风险
警告:系统检测到您的账号存在安全风险
为了保护您的账号安全,请在“赏学吧”公众号进行验证,点击“官网服务”-“账号验证”后输入验证码“”完成验证,验证成功后方可继续查看答案!
